Advantages Of Wireshark Tool
ISA/VPNQ2006/ics_wireshark_ping_3_big.png' alt='Advantages Of Wireshark Tool' title='Advantages Of Wireshark Tool' />
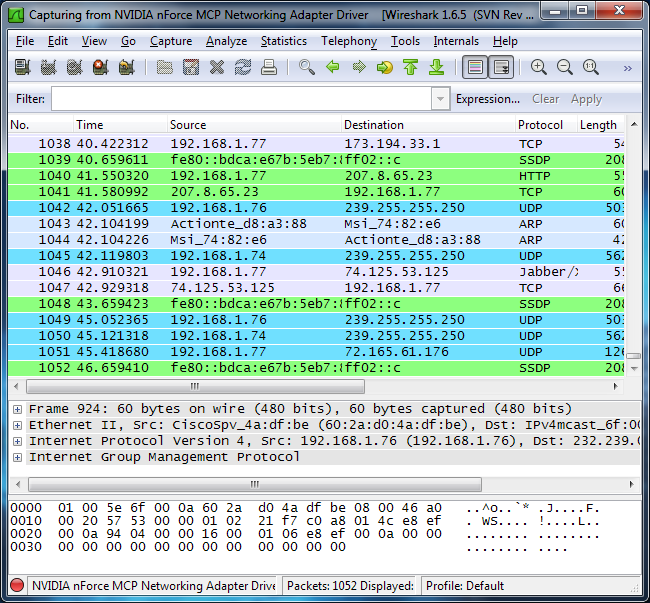 Windows 2. R2 server. Hello experts. I have several entries in my Security logs of a hacking attempt. Initially I thought it may be an owa brute force attack. There is nothing in the IIS logs that correlate to this timestamp, and the Loginprocess is Nt. Lm. Ssp rather than Advapi. Any advice on how to track the source of this hack attempt would be greatly appreciated. I will save some of your life for network sniffing when a hard bug bits you. Please, put wireshark in the bin. Here are two better alternative, sadly undervalued and. Ok, I am completely baffled here. We are replacing a Forefront TMG firewall with a SonicWall NSA 2600. We have a block of fixed IPs 5 from our provider. THE CAR HACKERS HANDBOOK. A Guide for the Penetration Tester. Craig Smith. Monitoring WAN links for availability and reliability is essential business organizations absolutely require continuous uptime, fast response times, and minimal. Attached is the logged event. Log Name Security. Source Microsoft Windows Security Auditing. Date 71. PMEvent ID 4. Task Category Logon. Level Information. Keywords Audit Failure. User NAComputer EXCH2. Description An account failed to log on. Subject Security ID NULL SIDAccount Name Account Domain Logon ID 0x. Logon Type 3. Account For Which Logon Failed Security ID NULL SIDAccount Name Account Domain foo. Failure Information Failure Reason Unknown user name or bad password. Status 0xc. Sub Status 0xc. Process Information Caller Process ID 0x. Caller Process Name Network Information Workstation Name ASMIRCRACKER1. Source Network Address Source Port Detailed Authentication Information Logon Process Nt. Lm. Ssp Authentication Package NTLMTransited Services Package Name NTLM only Key Length 0. This event is generated when a logon request fails. It is generated on the computer where access was attempted. WireShark_ERSPAN_example_capture.png' alt='Advantages Of Wireshark Tool' title='Advantages Of Wireshark Tool' />Instead of focusing on specific exploits and malware that quickly become outdated, Advanced Network Forensics taught me about the full range of evidence sources. WgZXNstgUvs/hqdefault.jpg' alt='Advantages Of Wireshark Tool' title='Advantages Of Wireshark Tool' />The Subject fields indicate the account on the local system which requested the logon. This is most commonly a service such as the Server service, or a local process such as Winlogon. Services. exe. The Logon Type field indicates the kind of logon that was requested. The most common types are 2 interactive and 3 network. The Process Information fields indicate which account and process on the system requested the logon. The Network Information fields indicate where a remote logon request originated. Workstation name is not always available and may be left blank in some cases. The authentication information fields provide detailed information about this specific logon request. Transited services indicate which intermediate services have participated in this logon request. Package name indicates which sub protocol was used among the NTLM protocols. Key length indicates the length of the generated session key. This will be 0 if no session key was requested. Event Xml lt Event xmlnshttp schemas. System lt Provider NameMicrosoft Windows Security Auditing Guid5. A5. BA 3. E3. B0. C3. 0D lt Event. ID 4. Event. ID lt Version 0lt Version lt Level 0lt Level lt Task 1. Task lt Opcode 0lt Opcode lt Keywords 0x. Keywords lt Time. Created System. Time2. T2. 2 0. 0 3. 5. Z lt Event. Record. ID 5. Event. Record. ID lt Correlation lt Execution Process. ID5. 52 Thread. ID6. Channel Securitylt Channel lt Computer EXCH2. Computer lt Security lt System lt Event. Data lt Data NameSubject. User. Sid S 1 0 0lt Data lt Data NameSubject. User. Name lt Data lt Data NameSubject. Domain. Name lt Data lt Data NameSubject. Logon. Id 0x. Data lt Data NameTarget. Telecharger Les Chevaliers Du Zodiaque Le Sanctuaire Film on this page. User. Sid S 1 0 0lt Data lt Data NameTarget. User. Name lt Data lt Data NameTarget. Domain. Name foo. Data lt Data NameStatus 0xc. Data lt Data NameFailure. Reason 2. 31. Data lt Data NameSub. Status 0xc. 00. Data lt Data NameLogon. Type 3lt Data lt Data NameLogon. D Day there. Process. Name Nt. Lm. Ssp lt Data lt Data NameAuthentication. Package. Name NTLMlt Data lt Data NameWorkstation. Name ASMIRCRACKER1lt Data lt Data NameTransmitted. Services lt Data lt Data NameLm. Package. Name lt Data lt Data NameKey. Length 0lt Data lt Data NameProcess. Id 0x. 0lt Data lt Data NameProcess. Name lt Data lt Data NameIp. Address lt Data lt Data NameIp. Port lt Data lt Event.
Windows 2. R2 server. Hello experts. I have several entries in my Security logs of a hacking attempt. Initially I thought it may be an owa brute force attack. There is nothing in the IIS logs that correlate to this timestamp, and the Loginprocess is Nt. Lm. Ssp rather than Advapi. Any advice on how to track the source of this hack attempt would be greatly appreciated. I will save some of your life for network sniffing when a hard bug bits you. Please, put wireshark in the bin. Here are two better alternative, sadly undervalued and. Ok, I am completely baffled here. We are replacing a Forefront TMG firewall with a SonicWall NSA 2600. We have a block of fixed IPs 5 from our provider. THE CAR HACKERS HANDBOOK. A Guide for the Penetration Tester. Craig Smith. Monitoring WAN links for availability and reliability is essential business organizations absolutely require continuous uptime, fast response times, and minimal. Attached is the logged event. Log Name Security. Source Microsoft Windows Security Auditing. Date 71. PMEvent ID 4. Task Category Logon. Level Information. Keywords Audit Failure. User NAComputer EXCH2. Description An account failed to log on. Subject Security ID NULL SIDAccount Name Account Domain Logon ID 0x. Logon Type 3. Account For Which Logon Failed Security ID NULL SIDAccount Name Account Domain foo. Failure Information Failure Reason Unknown user name or bad password. Status 0xc. Sub Status 0xc. Process Information Caller Process ID 0x. Caller Process Name Network Information Workstation Name ASMIRCRACKER1. Source Network Address Source Port Detailed Authentication Information Logon Process Nt. Lm. Ssp Authentication Package NTLMTransited Services Package Name NTLM only Key Length 0. This event is generated when a logon request fails. It is generated on the computer where access was attempted. WireShark_ERSPAN_example_capture.png' alt='Advantages Of Wireshark Tool' title='Advantages Of Wireshark Tool' />Instead of focusing on specific exploits and malware that quickly become outdated, Advanced Network Forensics taught me about the full range of evidence sources. WgZXNstgUvs/hqdefault.jpg' alt='Advantages Of Wireshark Tool' title='Advantages Of Wireshark Tool' />The Subject fields indicate the account on the local system which requested the logon. This is most commonly a service such as the Server service, or a local process such as Winlogon. Services. exe. The Logon Type field indicates the kind of logon that was requested. The most common types are 2 interactive and 3 network. The Process Information fields indicate which account and process on the system requested the logon. The Network Information fields indicate where a remote logon request originated. Workstation name is not always available and may be left blank in some cases. The authentication information fields provide detailed information about this specific logon request. Transited services indicate which intermediate services have participated in this logon request. Package name indicates which sub protocol was used among the NTLM protocols. Key length indicates the length of the generated session key. This will be 0 if no session key was requested. Event Xml lt Event xmlnshttp schemas. System lt Provider NameMicrosoft Windows Security Auditing Guid5. A5. BA 3. E3. B0. C3. 0D lt Event. ID 4. Event. ID lt Version 0lt Version lt Level 0lt Level lt Task 1. Task lt Opcode 0lt Opcode lt Keywords 0x. Keywords lt Time. Created System. Time2. T2. 2 0. 0 3. 5. Z lt Event. Record. ID 5. Event. Record. ID lt Correlation lt Execution Process. ID5. 52 Thread. ID6. Channel Securitylt Channel lt Computer EXCH2. Computer lt Security lt System lt Event. Data lt Data NameSubject. User. Sid S 1 0 0lt Data lt Data NameSubject. User. Name lt Data lt Data NameSubject. Domain. Name lt Data lt Data NameSubject. Logon. Id 0x. Data lt Data NameTarget. Telecharger Les Chevaliers Du Zodiaque Le Sanctuaire Film on this page. User. Sid S 1 0 0lt Data lt Data NameTarget. User. Name lt Data lt Data NameTarget. Domain. Name foo. Data lt Data NameStatus 0xc. Data lt Data NameFailure. Reason 2. 31. Data lt Data NameSub. Status 0xc. 00. Data lt Data NameLogon. Type 3lt Data lt Data NameLogon. D Day there. Process. Name Nt. Lm. Ssp lt Data lt Data NameAuthentication. Package. Name NTLMlt Data lt Data NameWorkstation. Name ASMIRCRACKER1lt Data lt Data NameTransmitted. Services lt Data lt Data NameLm. Package. Name lt Data lt Data NameKey. Length 0lt Data lt Data NameProcess. Id 0x. 0lt Data lt Data NameProcess. Name lt Data lt Data NameIp. Address lt Data lt Data NameIp. Port lt Data lt Event.